I was preparing to knock off work for the week on a recent Friday evening when a curious and annoying email came in via the contact form on this site:
“Hello I go by the username Nuclear27 on your site Briansclub[.]com,” wrote “Mitch,” confusing me with the proprietor of perhaps the underground’s largest bazaar for stolen credit and identity data. “I made a deposit to my wallet on the site but nothing has shown up yet and I would like to know why.”

The real BriansClub login page.
Several things stood out in Mitch’s message. For starters, that is not the actual domain for BriansClub. And it’s easy to see why Mitch got snookered: The real BriansClub site is currently not at the top of search results when one queries that shop name at Google.
Also, this greenhorn criminal clearly had bought into BriansClub’s advertising, which uses my name and likeness in a series of ads that run on all the top cybercrime forums. In those ads, a crab with my head on it zigs and zags on the sand. This is all meant to be a big joke: Krebs means “crab” or “cancer” in German, but a “crab” is sometimes used in Russian hacker slang to refer to a “carder,” or a person who regularly engages in street-level credit card fraud. Like Mitch.
In late 2019, BriansClub changed its homepage to include doctored images of my Social Security and passport cards, credit report and mobile phone bill information. That was right after KrebsOnSecurity broke the news that someone had hacked BriansClub and siphoned information on 26 million stolen debit and credit accounts. The hacked BriansClub database had an estimated collective street value of $566 million, and that data was subsequently shared with thousands of financial institutions.
Mitch said he’d just made a deposit of $240 worth of bitcoin at BriansClub[.]com, and was wondering when the funds would be reflected in the balance of his account on the shop.
Playing along, I said I was sorry to hear about his ordeal, and asked Mitch if there were any stolen cards issued by a particular bank or to a specific region that he was seeking.
Mitch didn’t bite, but neither would he be dissuaded that I was at fault for his wayward funds. He shared a picture showing funds he’d sent to the bitcoin address instructed by BriansClub[.]com — 1PLALmM5rrmLTGGVRHHTnB6VnZd3FFwh1Z — using a Bitcoin ATM in Canada.
The real BriansClub uses a dodgy virtual currency exchange service based in St. Petersburg, Russia called PinPays. The company’s website has long featured little more than a brand icon and an instant messenger address to reach the proprietor. The fake BriansClub told Mitch the Bitcoin address he was asked to pay was a PinPays address that would change with each transaction.

The payment message displayed by the carding site phishing domain BriansClub[.]com.
However, upon registering at the phishing site and clicking to fund my account, I was presented with the exact same Bitcoin address that Mitch said he paid. Also, the site wasn’t using PinPays; it was just claiming to do so to further mimic the real BriansClub.
According to the Blockchain, that Bitcoin address Mitch paid has received more than a thousand payments over the past five months totaling more than USD $40,000 worth of Bitcoin. Most are relatively small payments like Mitch’s.
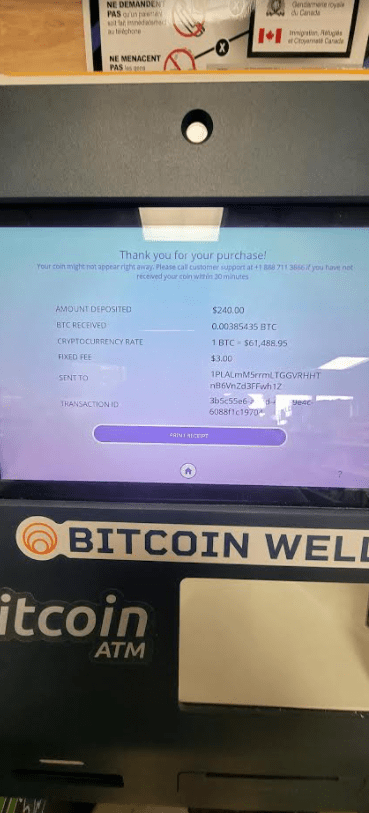
The screenshot Mitch sent of his deposit.
Unwary scammers like Mitch are a dime a dozen, as are phishing sites that spoof criminal services online. Shortly after it came online as a phishing site last year, BriansClub[.]com was hosted at a company in Moscow with just a handful of other domains phishing popular cybercrime stores, including Jstashbazar[.]com, vclub[.]cards, vclubb[.]com and vclub[.]credit.
Whoever’s behind these sites is making a decent income fleecing clueless crooks. A review of the Bitcoin wallet listed as the payment address for BriansClub[.]org, for example, shows a similar haul: 704 transactions totaling $38,000 in Bitcoin over the past 10 months.
“Wow, thanks for ripping me off,” Mitch wrote, after I’d dozed off for the evening without responding to his increasingly strident emails. “Should have spent the last money on my bills I’m trying to pay off. Should have known you were nothing but a thief.”
Deciding the ruse had gone too far, I confessed to Mitch that I wasn’t really the administrator of BriansClub, and that the person he’d reached out to was an independent journalist who writes about cybercrime. I told him not to feel bad, as more than a thousand people had been similarly duped by the carding shop.
But Mitch did not appear to accept my confession.
“If that’s the case then why is your name all over it including in the window that opens up when you go to make a deposit?,” Mitch demanded, referring to the phishing site.
Clearly, nothing I said was going to deter Mitch at this point. He asked in a follow-up email if a link he included in the message was indeed the “legitimate” BriansClub address. My only reply was that he should maybe consider another line of work before he got ripped off yet again, or the Royal Canadian Mounted Police showed up at his doorstep.
Scammers who fall for fake carding sites can expect to have their accounts taken over at the real shop, which usually means someone spends your balance on stolen cards. But mostly, these imposter carding sites are asking new members to fund their accounts by making deposits in virtual currency like Bitcoin.
In 2018, KrebsOnSecurity examined a huge network of phishing sites masquerading as the top carding stores which all traced back to a web development group in Pakistan that’s apparently been stealing from thieves for years.
As I noted in that piece, creating a network of fake carding sites is the perfect cybercrime. After all, nobody who gets phished or scammed is going to report the crime to the authorities. Nor will anyone help the poor sucker who gets snookered by one of these fake carding sites. Caveat Emptor!
The most one can hope for is that the occasional enterprising phisher is brought to justice. While it may be hard to believe that authorities would go after crooks stealing from one another, in 2017 a Connecticut man pleaded guilty to charges of phishing several criminal dark web markets in a scheme that eventually netted over $365,000 and more than 10,000 stolen user credentials.
And what about the provenance of the phishing domain briansclub[.]com? Looking closer at the original WHOIS registration records for briansclub[.]com via DomainTools (an advertiser on this site), we can see it was registered in November 2015 — several months after the real BriansClub came online. It was registered to a “Brian Billionaire,” a.k.a. Brian O’Connor, an apparently accomplished music deejay, rapper and rap music producer in Florida.

Brian Billionaire.
For several years after it came online, BriansClub[.]com and other domains apparently registered to Mr. Billionaire redirected to his main site — newhotmusic.com, which predates the carding shop BriansClub and also has a members-only section of the site called Brian’s Club.
Mr. Billionaire did not respond to multiple requests for comment, but it looks like his only crime is being a somewhat cringeworthy DJ. DomainTools’ record for briansclub[.]com says the domain was abandoned or dormant for a period in 2019, only to be scooped up again by someone in May 2020 when it became a phishing site spoofing the real BriansClub.